What are you looking for?
Can Your Network Handle The Truth?
Find out how your network stacks up
Truth is Important
The modern world requires fast-paced reactions to both business and technical challenges. Unfortunately, some designs and vendor solutions don't work correctly. For instance, some network data monitoring solutions drop packets causing security threats to become obscured. If you don't know what is real, how can you react appropriately to the market and your internal and external customers? The only way to know is to validate your existing architecture.
As an example, can you definitively answer these questions about your network:
- Can it handle data rates of 100 Gbps and beyond?
- Are you meeting customer, troubleshooting, and performance SLAs?
- Is your network really secure and can you prove it?
Keysight solutions solve these, and many more, problems for you. With 100% network visibility from Keysight, your security and performance monitoring solutions get all the data they need to deliver results. Keysight delivers data from every network segment, every type of cloud, encrypted or not, and filters that data at line-rate speed to increase efficiency.
So, how does your network measure up? Find out the truth with Keysight.
Visibility Matters
Bad Things Happen When You Are In The Dark
Network visibility is paramount to your ability to quickly discover and isolate faults. The longer it takes you to figure out what happened and react, means the longer your network is down or operating in a diminished state. This impacts company revenue, company reputation and network security. Use taps and network packet brokers (NPBs) to give you the network visibility you need and deserve. You can't protect what you can't see.
See every packet with Keysight NPBs and Flex taps.
Every Network Is Vulnerable
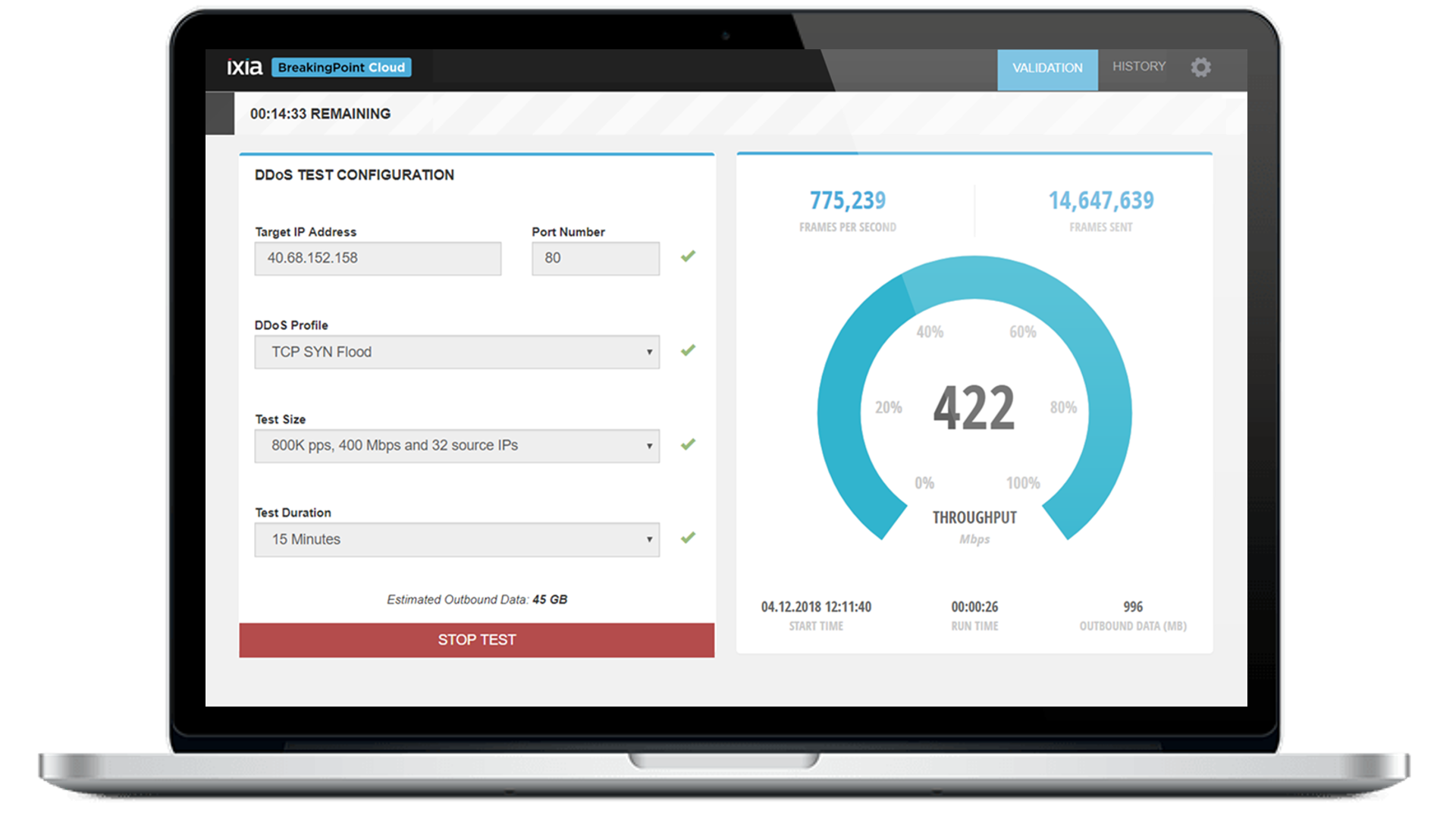
According to some industry experts, it is not a case of “if” your network will be beached or not, but “when” will it be breached, and will you know about the breach? This is why it is incredibly important to understand the baseline operation of your network and then to routinely validate that it works as designed. Solutions from Keysight like BreakingPoint and Threat Simulator allow you to verify the security efficacy of your network in both pre-deployment and post-deployment scenarios. Other solutions like bypass switches and inline network packet brokers allow you to further protect the network and implement cyber resilience.
Dig Deeper
Keysight University
Free on-demand learning and certification for engineers at every level.
- Learn engineering essentials
- Understand the fundamentals of using your lab equipment
- Broaden your advanced measurement knowledge with boot camps
Want help or have questions?