What are you looking for?
SDN, NFV, and Virtualization
Accelerate SDN, NFV, and virtualization success
SDN and NFV Solutions Help Maintain Visibility in the New Software Defined Data Center
SDN, NFV, and Virtualization For Enterprises
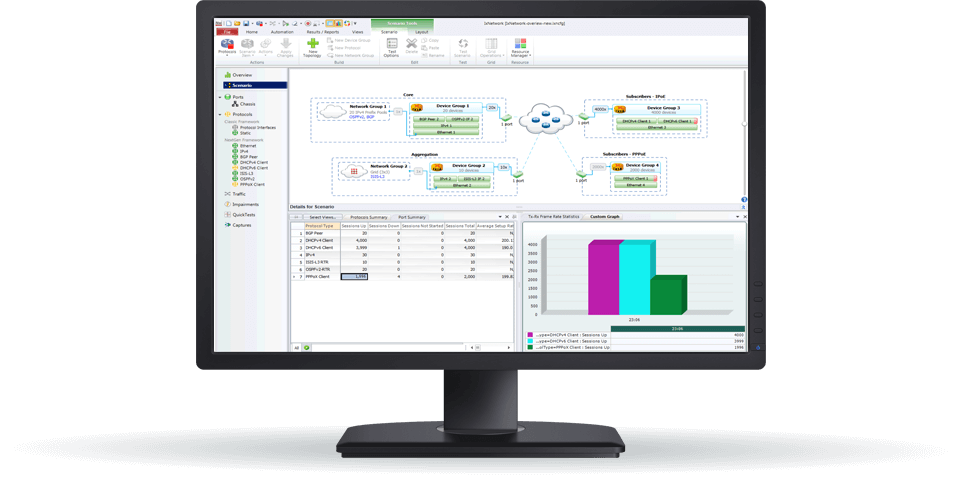
Virtualization and SDN increase your network utilization and agility. Getting visibility, however, into this software-defined infrastructure to validate application performance is challenging.
Our software-defined network solutions provide complete network-level visibility letting you test your virtual and SDN deployments. Whether deploying your broader network using SDN or deploying an SD-WAN, make sure you test your network with realistic traffic.


SDN, NFV, and Virtualization For Service Providers
Virtualized, software-defined network, and network functions virtualization architectures allow service providers to respond with unmatched scale and speed. Visibility access to measure application performance, however, is a challenge in virtual environments.
Our solutions help ensure your SDN-NFV applications meet performance expectations. We also help you eliminate blind-spots in east/west and monitor encrypted traffic across your virtual and software-defined networks.
Migrate, Test, and Monitor Your SDN and NFV Virtualized Deployments
Improve Disaggregated Visibility
Disaggregated networking solutions allow you to run best-of-breed network operating systems on open switches. This approach can be very cost effective in software defined data centers.
If disaggregation works for the network itself, it may also be right for your network visibility requirements. Whether deployed at the edge or aggregation layers of the network, Ixia's Vision Edge OS provides an effective but affordable way to bring visibility, replication, load balancing, and dynamic filtering to your data center.


Start In The Lab. Prove In Production. Time To Revenue: 20% Faster.
Everyone wants to deploy faster, and agile development is key to making that happen. It is about creating an environment where developers can integrate their new code into a realistic environment to evaluate its stability and security functions. Getting this right can result in advancing to production 20% faster.
We give you tools for end-to-end validation of virtualization migrations to dramatically accelerate time from lab to production. By ensuring alignment with the Continuous Integration/Continuous Deployment (CI/CD) agile service development model, you can rapidly identify and resolve issues.
Tapping Into Your Virtual Data
Your security is only as good as the data it sees. You rely on your network security tools to analyze and protect your data. Our visibility solutions provide access to east-west data, and distribute it to the right security and monitoring tools at the right time. We provide more than just copies of raw data to your security, analytics and performance tools in any virtual environment—we filter what is relevant to the user or tool at the source.
The combination of Ixia virtual taps and virtual packet brokers delivers the total visibility you need. The virtual visibility tools supports packet and application flow filtering, NetFlow generation with advanced application identification and geographic location, secure sockets layer (SSL) decryption, load balancing, and many advanced packet processing capabilities, like deduplication, header stripping, and fragmentation.

-
“Phantom Virtual Network Tap not only preserves the value of our instrumentation layer, it’s helping us save jobs as we virtualize. These economies are enormous.”
SR. NETWORK MANAGER, ENERGY PROVIDER
-
“We gained total visibility, a familiar management interface, and one vendor for physical and virtual architectures.”
CTO, ENERGY ENTERPRISE
-
“Ixia’s (now part of Keysight) virtualization solution and VMware together solve east-west traffic invisibility and attack vulnerabilities at the hypervisor kernel level.”
SENIOR VIRTUAL NETWORK ANALYST
Further Reading
Related Products
Want help or have questions?