What are you looking for?
EXata Network Modeling – Cyber
Evaluate a network design for resilience to cyber attack
Starting from
Highlights
Protect and Defend Critical Networks
The likelihood of cyber attacks with dramatic consequences makes cyber resilience critical. From commercial enterprise, IoT to military networked systems operating from the seabed to space, proactive and preemptive measures must be taken.
Our trusted software helps protect and defend critical networks using EXata Network Modeling – Cyber (EXata Cyber). Learn how critical communication networks will behave when under cyber attack and continuously assess network vulnerabilities from emerging threats in a cost-effective, and low-risk manner.
Benefits of EXata Cyber
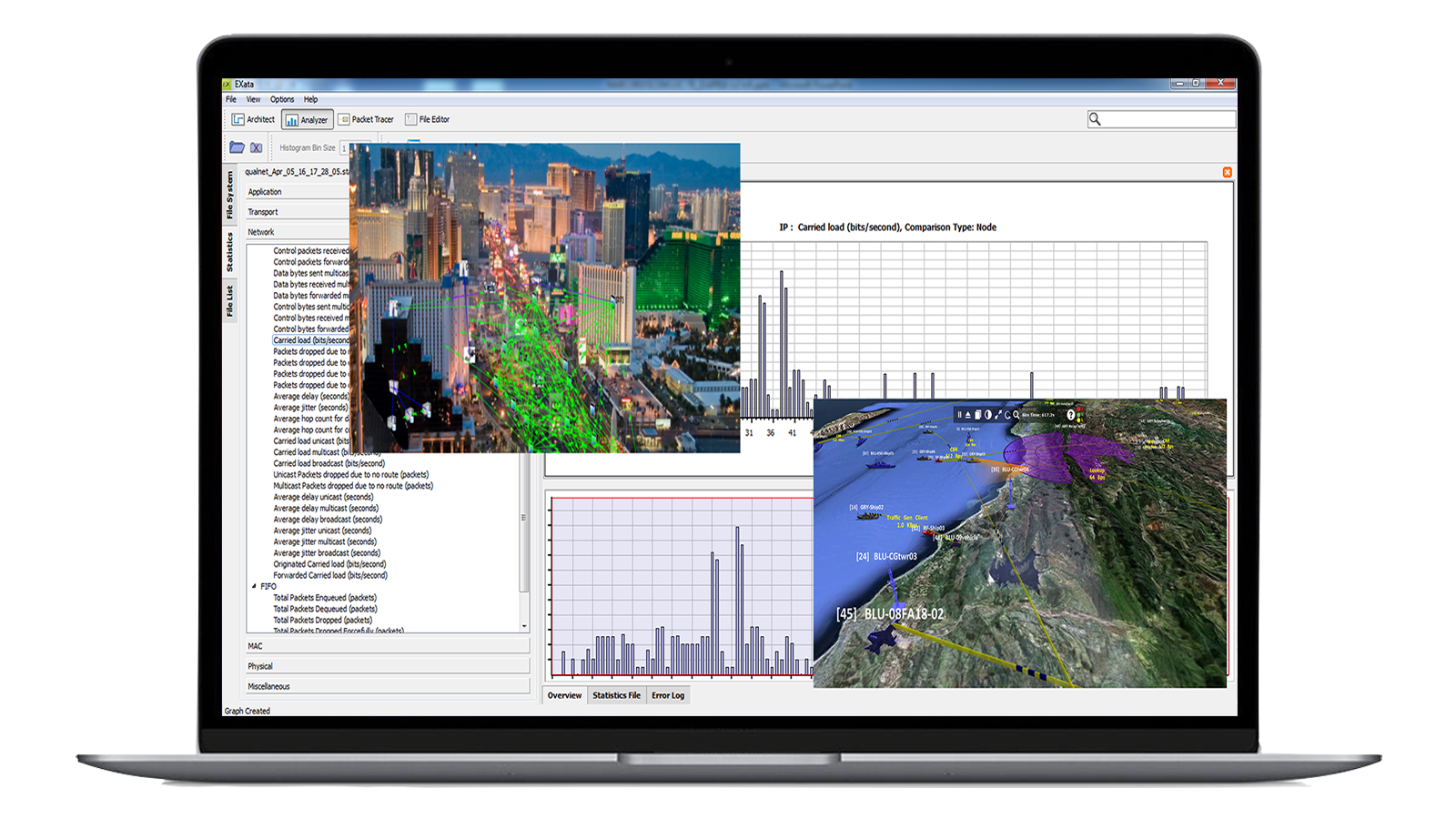
Every aspect of a cyber attack can be modeled and prepared for using our network digital twin cyber resilience tools. From IPSec and WEP to certificates, firewall, and public key infrastructure, there are plenty of models available in our expansive library. EXata Cyber offers the perfect blend of reliable emulation software and ample cyber capabilities to create an accurate network digital twin to improve security and protect vital networks from cyber threats.
- Gain unique visibility into how a network will respond during a cyber attack
- Launch cyber warfare features on a model, including eavesdropping, radio jamming attacks, distributed denial of service (DDoS) attacks, and a variety of attacks detectable with 3rd part network intrusion detection software (NIDS) like snort
- Ultra-high fidelity simulated representations of large scale wireless, wired and mixed-platform network performance and behavior
- Create sophisticated live-virtual constructive (LVC) environments with seamless integration of virtual models and live equipment and applications


Enhancing Wargaming Fidelity
Wargames must incorporate real-world cyber, communications, and networking effects to support the development of effective operating concepts, capabilities, and plans. The leading professional operational wargame, Command Professional Edition, takes advantage of the EXata Cyber and its extremely powerful cyber, communications, and networking capabilities.
We deliver enhanced wargame fidelity in a low-cost and zero-risk environment, helping improve knowledge and insights gained from wargame execution.
Cyber Attack Editor
Cyber resilience is becoming a key metric for all network deployments. The cyber-attack editor allows the user to design a library of historical or zero-day attacks using a no-code paradigm. Using this editor, users can direct distributed and adaptive network-wide attack vectors and assess the impact of vulnerabilities on key performance metrics.
Our enhanced cyber model library includes phishing, ransomware, data-stealing attack in host model, a Human- in-the-loop application for receiving malicious email, triggering host model attacks, and a GUI interface to create and manage adaptive attack scripts visually.


Facilitating Maritime Communications with Network modeling
EXata cyber enables users to accurately simulate cyber attacks on a variety of virtual networks, including those used in maritime communications to maintain secure communications by testing the resilience of multi-domain networks.
Live, Virtual, Constructive (LVC) network models let you test undersea communications networks, wireless communications networks, and sensors. Learn if they are vulnerable to certain atmospheric conditions, acoustic comms affected by sea states, and other network conditions that may impact communications in these unique environments.
Extend the Capabilities of Your SN100CYLA
Featured Resources
Want help or have questions?