Choose a country or area to see content specific to your location
-
PRODUCTS AND SERVICES
-
Oscilloscopes
-
Analyzers
- Spectrum Analyzers (Signal Analyzers)
- Network Analyzers
- Logic Analyzers
- Protocol Analyzers and Exercisers
- Bit Error Ratio Testers
- Noise Figure Analyzers and Noise Sources
- High-Speed Digitizers and Multichannel DAQ Solutions
- AC Power Analyzers
- DC Power Analyzers
- Materials Test Equipment
- Device Current Waveform Analyzers
- Parameter / Device Analyzers and Curve Tracers
-
Meters
-
Generators, Sources, and Power Supplies
-
Software
-
Wireless
-
Modular Instruments
-
Network Test and Security
-
Network Visibility
-
Services
-
Additional Products
- All Products, Software, Services
-
- Learn
- Support
What are you looking for?
- Home
- Industries
- Government, Finance, and Enterprise
- Enterprise
- Zero Trust Network Security
Building a Foundation for Zero Trust
Support your entire security lifecycle from Network Visibility to Continuous Validation
Zero Trust
The industry has seen a growing trend around a security concept called Zero Trust. Zero Trust is not a singular point product, but rather a combination of different solutions working in concert with one another. Whether you have already implemented Zero Trust in your organization or you are just at the early stages of your journey, Keysight is a partner you can trust.

Zero Trust Defined
"Trust No One, Verify All"
Zero Trust is a set of guiding principles that validates all users trying to access business resources regardless of who they are and where they’re from. Zero Trust turns the traditional network perimeter model on its head and converts it to a more data centric model with security controls every step of the way.

Zero Trust Verified
Needed More Than Ever
Various Zero Trust models are increasingly being adopted by enterprises and government security teams around the world. With perimeter security no longer effective by itself, new cloud models, the continued rise and sophistication of cyber attacks and current WFH initiatives, a Zero Trust architecture and corporate culture is needed now more than ever.

Network Segmentation
Segment, isolate, monitor and control the network

Device Management
Isolate, secure and control all devices accessing enterprise resources

Visibility & Analytics
Complete data collection and delivery with useful analytics

Automation & Orchestration
Automate Zero Trust elemets and provide more control over disparate systems
Every Network Is Vulnerable
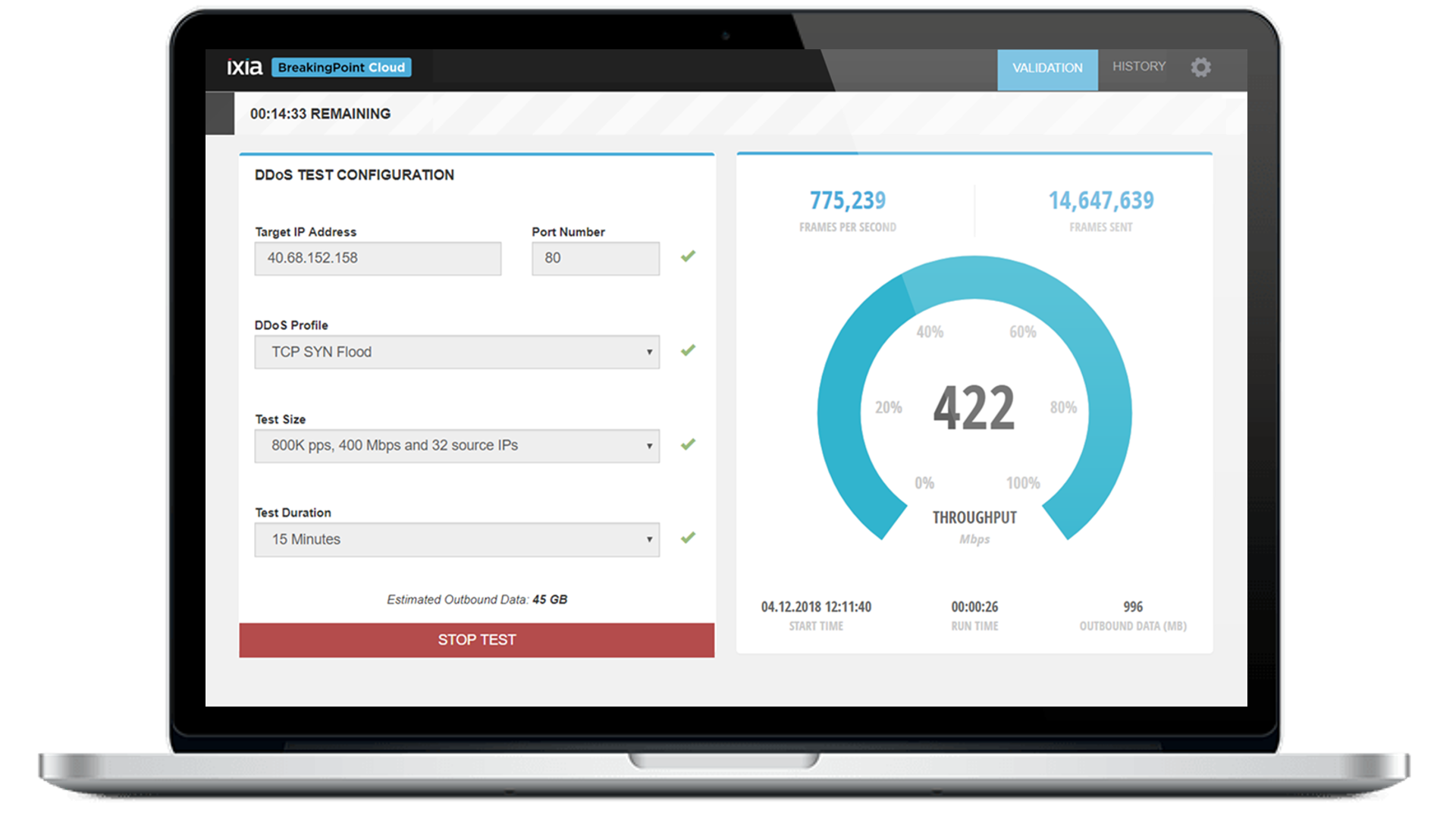
According to some industry experts, it is not a case of “if” your network will be beached or not, but “when” will it be breached, and will you know about the breach? This is why it is incredibly important to understand the baseline operation of your network and then to routinely validate that it works as designed. Solutions from Keysight like BreakingPoint and Threat Simulator allow you to verify the security efficacy of your network in both pre-deployment and post-deployment scenarios. Other solutions like bypass switches and inline network packet brokers allow you to further protect the network and implement cyber resilience.
See for yourself how you can optimize your network security.

Keysight Zero Trust Solutions
Network Security Threats You Need To Be Thinking About This Year
Help strengthen your cybersecurity practices by looking into three core attack vectors used in 2020. The Keysight Technologies 2021 Security Report gives you what you need to know to thwart those attacks. The report also discusses emerging threats for 2021.

.
Why Keysight Zero Trust
Focused on complete lifecycle protection, Keysight Zero Trust offers an effective solution set that is designed to secure all access to the network and applications, from any user and device from any location, while continuously testing the efficacy of the architecture and its policies. Our complimentary suite of products are designed to seamlessly interoperate with your entire infrastructure while maintaining your investments in other solutions.
Keysight Zero Trust Solutions

Enable Proactive Monitoring
Your approach to monitoring can leave you vulnerable to the unexpected.
Dig Deeper

Taps Versus Spans
Location, Location, Location
Want help or have questions?
- © Keysight Technologies 2000–2024
- Privacy
- Sitemap
- Terms
- Trademark Acknowledgements
- Feedback
- Accessibility